We are using the “Scheduled Config Export” feature of Panorama to backup the configuration to an FTP server internally. However when I run the backup I get the following error:
‘Failed to export config bundle file PANORAMA_20220812.tgz to host XXXXXX.XXXXXXX.XXXXXXX port 21 user PanoramaBackupUser passive-mode yes, error code 67’
We were not able to determine the issue and had to create a case with Palo Alto support. They confirmed that this is an issue with version 10.2.2 of Panorama and has been resolved in version 10.2.3. I upgraded our appliance this morning and now this is working as expected.
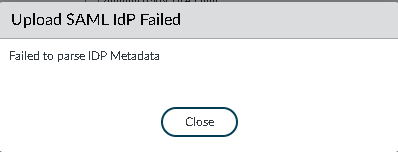
When setting up SAML IDP on Palo Alto firewall (version 10.0.6) we are importing the XML file provided by our SAML vendor.
However, when importing it we get the following error message:
Upload SAML IDP Failed
Failed to parse IDP Metadata.
The problem is that the “Profile Name” field is limited to 31 characters, but it isn’t validated by the firewall. From the validation when making a new SAML Identity Provider, only alphanumeric characters, underscore ‘_’, hyphen ‘-‘, dot ‘.’ or spaces are permitted.
If you decrease the length of the name, it will import the metadata correctly.
I deployed a Palo Alto VM firewall into Azure recently. Every time I deployed it from the Azure template from the Marketplace or using bootstrap (which still uses the Azure template to get started) the firewall would take about 20-30 minutes and then wind up in maintenance mode without a usable IP address, and no management GUI.
Errors on the serial console were “Entry Reason: System Startup error.” and the Maintenance Entry Reason was “System start failed multiple times. Caused by service: mgmtsrvr”. I deployed the latest version of Palo Alto firewall (version 9.1.3 as of this writing).
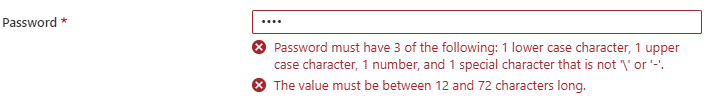
Eventually I was able to solve the problem by trying a different password. Even though the template has the following requirements for passwords:
![]()

Our original auto generated password that broke the firewall was ![]() “wQCoPb7E7T9c5844FbbA@r5iVFQu8V2S” (no quotes). I don’t know if the @ (asterisk) symbol broke the firewall or there was a length issue, but after we changed the password the firewall deployed quickly and easily into Azure. So if you are immediately kicked into maintenance mode with your Palo Alto firewall, try a different password.
“wQCoPb7E7T9c5844FbbA@r5iVFQu8V2S” (no quotes). I don’t know if the @ (asterisk) symbol broke the firewall or there was a length issue, but after we changed the password the firewall deployed quickly and easily into Azure. So if you are immediately kicked into maintenance mode with your Palo Alto firewall, try a different password.
What interests me now on the Internet


