I deployed a Palo Alto VM firewall into Azure recently. Every time I deployed it from the Azure template from the Marketplace or using bootstrap (which still uses the Azure template to get started) the firewall would take about 20-30 minutes and then wind up in maintenance mode without a usable IP address, and no management GUI.
Errors on the serial console were “Entry Reason: System Startup error.” and the Maintenance Entry Reason was “System start failed multiple times. Caused by service: mgmtsrvr”. I deployed the latest version of Palo Alto firewall (version 9.1.3 as of this writing).
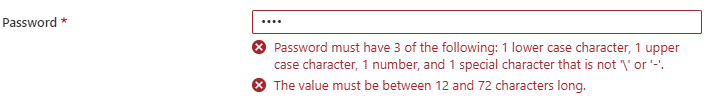
Eventually I was able to solve the problem by trying a different password. Even though the template has the following requirements for passwords:
![]()
Our original auto generated password that broke the firewall was “wQCoPb7E7T9c5844FbbA@r5iVFQu8V2S” (no quotes). I don’t know if the @ (asterisk) symbol broke the firewall or there was a length issue, but after we changed the password the firewall deployed quickly and easily into Azure. So if you are immediately kicked into maintenance mode with your Palo Alto firewall, try a different password.